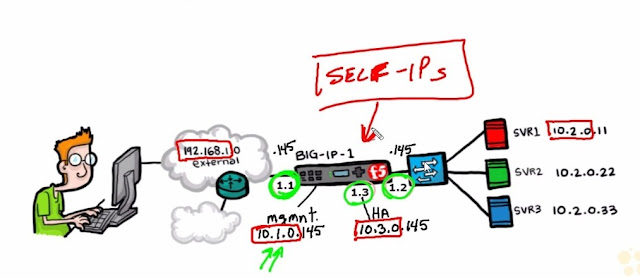
We will use this network diagram for this lab.
The IPsec VPN will be created between Outside-R and the ASAv.
Traffic from 192.168.20.0/24 and 10.1.1.0/24 subnets will be encrypted using the tunnel.
The tricky part on the ASA is that ASDM doesn't allow you to remove or let's say limit the number of cipher suits to be used with the IPsec tunnel which is the phase-2 of the IPsec IKEv1. It'll be clear with the CLI below.
Here's the VPN config on the IOS router.
Here's the ASA config from the CLI anyway.
Let's see the IOS router debug first.
Which means NOTIFY PROPOSAL_NOT_CHOSEN is a phase-2 problem. And the reason is a mismatch between the ciphers used for the phase 2 negotiation.
Refer back to the config lines on both the devices we see:
crypto ipsec transform-set ourset esp-aes - router
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-MD5 - ASA
These lines show control the phase-2 cipher negotiation and both do look the same, here the part which I omitted from the ASA config comes in to play.
Here's the complete ASA config from the CLI
The whole confusion is that the ASDM doesn't properly display this and the only thing you see there is just a single cipher.
Maybe this is a bug or I missed something. But for now to get this VPN to work you simply have to remove all the other non-matching ciphers with a "no" command in the ASA CLI.
That is just keep the one cipher which is highlighted or whichever you use in your case.
This entire confusion is because of the way ASDM displays the ciphers. I hope to find more info on that and update this further.
The IPsec VPN will be created between Outside-R and the ASAv.
Traffic from 192.168.20.0/24 and 10.1.1.0/24 subnets will be encrypted using the tunnel.
The tricky part on the ASA is that ASDM doesn't allow you to remove or let's say limit the number of cipher suits to be used with the IPsec tunnel which is the phase-2 of the IPsec IKEv1. It'll be clear with the CLI below.
Here's the VPN config on the IOS router.
For the ASA config it's highly recommended to just use the IPsec VPN wizard from the wizards menu.Outside-R#show running-config | section crypto crypto isakmp policy 1 encr aes hash md5 authentication pre-share group 2 crypto isakmp key cisco address 0.0.0.0 0.0.0.0 crypto ipsec transform-set ourset esp-aes crypto map ourmap 1 ipsec-isakmp set peer 192.168.2.1 set transform-set ourset match address 100 crypto map ourmap
Here's the ASA config from the CLI anyway.
I have edited the ASA output to exclude a huge section which is unnecessary and which actually causes the problem.ciscoasa# show running-config cryptocrypto ipsec security-association pmtu-aging infinite crypto map outside_map 1 match address outside_cryptomap crypto map outside_map 1 set peer 192.168.2.2 crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-MD5 ESP-AES-128-MD5-TRANS crypto map outside_map interface outside crypto ca trustpool policy crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes hash md5 group 2 lifetime 86400
Let's see the IOS router debug first.
The highlighted part in the last line show us that Phase-1 is complete.Outside-R# debug crypto isakmp *Mar 1 03:15:12.955: ISAKMP:(1001): retransmitting phase 2 QM_IDLE 1349190959 ... *Mar 1 03:15:12.955: ISAKMP (0:1001): incrementing error counter on node, attempt 2 of 5: retransmit phase 2 *Mar 1 03:15:12.955: ISAKMP (0:1001): incrementing error counter on sa, attempt 2 of 5: retransmit phase 2 *Mar 1 03:15:12.955: ISAKMP:(1001): retransmitting phase 2 1349190959 QM_IDLE *Mar 1 03:15:12.959: ISAKMP:(1001): sending packet to 192.168.2.1 my_port 500 peer_port 500 (R) QM_IDLE *Mar 1 03:15:12.959: ISAKMP:(1001):Sending an IKE IPv4 Packet. *Mar 1 03:15:12.975: ISAKMP (0:1001): received packet from 192.168.2.1 dport 500 sport 500 Global (R) QM_IDLE *Mar 1 03:15:12.975: ISAKMP: set new node -619099427 to QM_IDLE *Mar 1 03:15:12.975: ISAKMP:(1001): processing HASH payload. message ID = -619099427 *Mar 1 03:15:12.975: ISAKMP:(1001): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3 spi 0, message ID = -619099427, sa = 66772820 *Mar 1 03:15:12.975: ISAKMP:(1001):deleting node -619099427 error FALSE reason "Informational (in) state 1" *Mar 1 03:15:12.975: ISAKMP:(1001):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY *Mar 1 03:15:12.975: ISAKMP:(1001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Which means NOTIFY PROPOSAL_NOT_CHOSEN is a phase-2 problem. And the reason is a mismatch between the ciphers used for the phase 2 negotiation.
Refer back to the config lines on both the devices we see:
crypto ipsec transform-set ourset esp-aes - router
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-MD5 - ASA
These lines show control the phase-2 cipher negotiation and both do look the same, here the part which I omitted from the ASA config comes in to play.
Here's the complete ASA config from the CLI
Now see the highlighted line above, that's the only cipher we need - because that's the one in use on the router or else the phase 2 negotiation won't match and we keep getting the error as shown in the debug.ciscoasa# show running-config crypto crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport crypto ipsec security-association pmtu-aging infinite crypto map outside_map 1 match address outside_cryptomap crypto map outside_map 1 set peer 192.168.2.2 crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-MD5 ESP-AES-128-MD5-TRANS crypto map outside_map interface outside crypto ca trustpool policy crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes hash md5 group 2 lifetime 86400
The whole confusion is that the ASDM doesn't properly display this and the only thing you see there is just a single cipher.
Maybe this is a bug or I missed something. But for now to get this VPN to work you simply have to remove all the other non-matching ciphers with a "no" command in the ASA CLI.
That is just keep the one cipher which is highlighted or whichever you use in your case.
no crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmacThat's it. Now your beautiful VPN tunnel will come up the moment you send the interesting traffic.
no crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
no crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
no crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
no crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
This entire confusion is because of the way ASDM displays the ciphers. I hope to find more info on that and update this further.